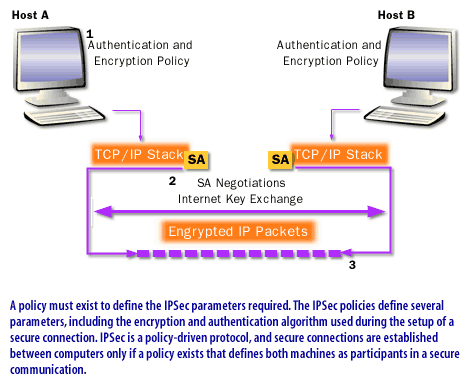
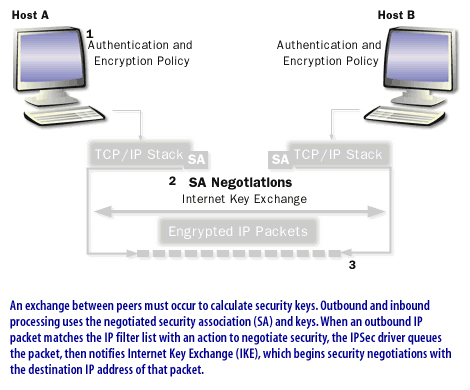
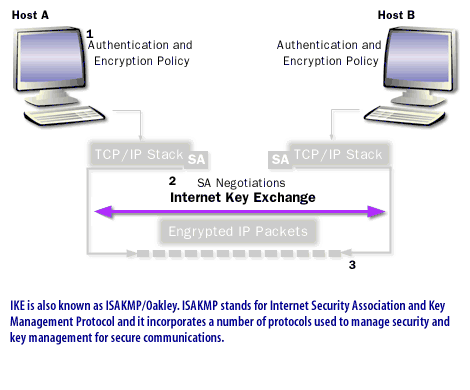
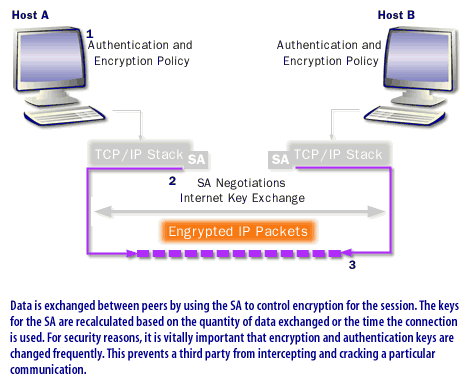
Protect data with IPSec
IPsec provides secure tunnels between two peers, such as two routers or switches.
More accurately, these tunnels are sets of security associations (SAs) that are established between two IPsec peers.
The SAs define which protocols and algorithms should be applied to sensitive packets and specify the keying material to be used by the two peers.
SAs are unidirectional and are established per security protocol (Authentication Header (AH) or Encapsulating Security Payload (ESP)). Multiple IPsec tunnels can exist between two peers to secure different data streams, with each tunnel using a separate set of SAs.
For example, some data streams might be authenticated only while other data streams must both be encrypted and authenticated.
Overview of IPSec