| Lesson 9 | Packet sniffing and tcpdump |
| Objective | Describe the type of information available from the output of the tcpdump program |
Packet Sniffing and TCP Dump
A packet sniffer is a program that reads all network traffic on a particular
network segment. Such a program is one of the most powerful tools available for network monitoring. The tcpdump program, which is widely available without cost, is one of the most highly developed packet sniffing programs.
Using tcpdump or other packet sniffers to their fullest capacity requires a sophisticated understanding of the TCP/IP protocols. Because TCP/IP is not the primary focus of this course, we will briefly discuss how tcpdump works and how it might be useful in debugging networking problems.
Using tcpdump or other packet sniffers to their fullest capacity requires a sophisticated understanding of the TCP/IP protocols. Because TCP/IP is not the primary focus of this course, we will briefly discuss how tcpdump works and how it might be useful in debugging networking problems.
Promiscuous mode
Ethernet is a broadcast protocol. On a single ethernet segment (such as an office or department local network), every piece of network traffic is “heard” by every node on the network. Under normal conditions, however, an ethernet interface will ignore all traffic not directed at it.If an ethernet interface is placed in “promiscuous mode,” it will pass all the network traffic it receives up to the protocol stack. This means that a node equipped with an appropriate program (such as tcpdump) can read all the network traffic on the segment, not just traffic intended for that particular node. This behavior has many important consequences for network security; any machine with physical access to an ethernet segment can examine every piece of data carried by that segment.
Running tcpdump
To put the ethernet device in promiscuous mode, tcpdump needs to run with root permissions.View the code below to examine a few typical lines from the tcpdump output.
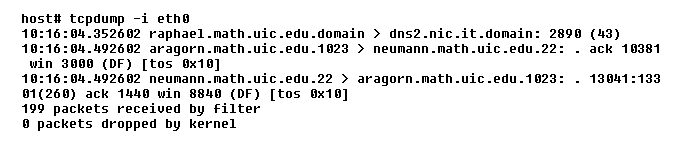
host# tcpdump -i eth0 10:16:04.352602 raphael.math.uic.edu.domain > dns2.nic.it.domain: 2896 (43) 10:16:04.492662 aragorn.math.uic.edu.1623 > neumann.math.uic.edu.22: . ack 10381 win 3000 (DF) [tos 0x10] 10:16:04.492662 neumann.math.uic.edu.22 > aragorn.math.uic.edu.1623: . 13041:133 61(268) ack 1440 win 8848 (DF) [tos 0x10] 199 packets received by filter 0 packets dropped by kernel
- Time stamp
- Packet's source host and port
- Packet's destination host and port
- Information from the packet's IP, TCP, or UDP headers
We will focus only on the source and destination part of the output. Interpreting the remaining part of the output is possible if you are familiar with the TCP and UDP protocols. On a busy network, the output from tcpdump may be overwhelming. Fortunately, the output may be filtered using a fairly sophisticated set of logical primitives. For example, to see telnet traffic coming into machine my_machine, you can use the command:
host# tcpdump –i eth0 dst host my_machine and dst port telnet
To see traffic between my_machine and your_machine, you may use:
host# tcpdump –i eth0 src host my_machine and dst host \ your_machine or src host your_machine and dst host my_machine
"tcpdump program" used by Linux Administrators to conduct Network Traffic Analysis
Yes, the "tcpdump" program is still widely used by Linux administrators for network traffic analysis, including tasks related to trace routing. While tcpdump itself does not perform trace routing, it can capture packets that are used by trace routing tools and processes, allowing administrators to analyze how data packets are routed through a network. Tcpdump is particularly valued for its powerful and detailed packet-sniffing capabilities, which help in diagnosing network issues, monitoring network traffic, and understanding traffic flow. For actual trace routing, tools like `traceroute` or `mtr` are typically used in conjunction with tcpdump for deeper analysis.
"IP tracing tool" and how it functions
An IP tracing tool, also known as an IP tracker or IP lookup tool, is a software or online service that helps identify the location and other information related to an Internet Protocol (IP) address.
Here's how it functions:
Keep in mind that IP tracing tools may not always provide accurate results, as IP addresses can be masked or spoofed using VPNs, proxies, or other techniques.
- IP Address Input: You enter the IP address you want to trace into the tool.
- Database Search: The tool searches its database or queries external databases to gather information about the IP address.
- Geolocation: The tool attempts to identify the physical location of the device associated with the IP address, including country, region, city, and postal code.
- ISP and Network Information: The tool may also provide information about the Internet Service Provider (ISP) and network details.
- Device and OS Information: Some tools may even try to identify the device type, operating system, and browser used by the device associated with the IP address.
- Results Display: The tool presents the gathered information in a user-friendly format, often including a map view of the location.
- Network troubleshooting and debugging
- Cybersecurity investigations and threat tracking
- Online fraud detection and prevention
- Marketing and analytics purposes (e.g., identifying user locations)
Keep in mind that IP tracing tools may not always provide accurate results, as IP addresses can be masked or spoofed using VPNs, proxies, or other techniques.
traceRoute tcpdump - Quiz
Click the Quiz link below to take a short multiple-choice quiz on traceroute and tcpdump.
Trace Route tcp Dump - Quiz
Trace Route tcp Dump - Quiz