| Lesson 4 | Internet layer (IP) |
| Objective | Identify the Internet layer and its weaknesses. |
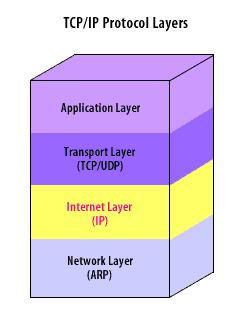
Internet Protocol Layer
The next layer of the TCP/IP stack is the Internet layer.
The Internet layer is used primarily for addressing hosts and for routing. It does not provide any means for error correction or flow control. The IP layer uses best-effort services to deliver IP datagrams .
The Internet layer is used primarily for addressing hosts and for routing. It does not provide any means for error correction or flow control. The IP layer uses best-effort services to deliver IP datagrams .
TCP/IP Internet layer
IP Layer Attacks
The open architecture of the IP layer makes it an easy target for hackers. Every IP datagram is an individual piece of
information traveling from one host to another. The hosts compile the received IP datagrams into a usable form. Because so
many protocols are in operation at once, it is easy to defeat the proper function of any one protocol.
IP spoofing
Hackers will often use a technique called IP spoofing, which is the process of replacing the source IP address with a false IP address. Because TCP/IP's open architecture has no built-in authentication, one host or machine can spoof another's identity. Source-routed IP datagrams, created to travel only a specific path, are used to circumvent security measures such as firewalls.
Another type of IP spoofing is known as a Smurf attack. A Smurf attack sends out a series of pings to a large number of remote hosts. All the remote computers respond to the ping and reply to a targeted IP address instead of to the attacker's true IP address. The target IP address is then inundated with Internet Control Message Protocol (ICMP) packets and can no longer function properly.
The ICMP is used to communicate errors or other conditions at the IP layer. For example, when a host is pinged to determine if it is operational, a ICMP message is generated.
The ICMP is used to communicate errors or other conditions at the IP layer. For example, when a host is pinged to determine if it is operational, a ICMP message is generated.
Click the link below to read more about attacks on the Internet control message protocol.
Internet Control Message Protocol
Internet Control Message Protocol
TCP/IP Protocols
The following definitions hold true for TCP/ IP Protocols:
- Internet protocol, Uses addressing to find a route so that datagrams reach the correct destination
- Transport protocol, Breaks information into datagrams and ensures that all datagrams arrive correctly
- Address resolution protocol, Converts IP addresses to physical network addresses by broadcasting an address request
- Internet control message protocol, Used to communicate errors or other conditions at the IP layer
The Internet protocol suite is the networking model and a set of communications protocols used for the Internet and similar networks.
It is commonly known as TCP/IP, because its most important protocols, the Transmission Control Protocol (TCP) and the Internet Protocol (IP), were the first networking protocols defined in this standard. It is occasionally known as the DoD model, because the development of the networking model was funded by DARPA, an agency of the United States Department of Defense. TCP/IP provides end-to-end connectivity specifying how data should be formatted, addressed, transmitted, routed and received at the destination.
This functionality has been organized into four abstraction layers which are used to sort all related protocols according to the scope of networking involved. From lowest to highest, the layers are the
This functionality has been organized into four abstraction layers which are used to sort all related protocols according to the scope of networking involved. From lowest to highest, the layers are the
- link layer,
- containing communication technologies for a single network segment (link),
- the internet layer,
- connecting independent networks,
- thus establishing internetworking,
- the transport layer handling process-to-process communication,
- and the application layer, which interfaces to the user and provides support services.
Smurf attacks are an example of a denial-of-service[1] attack.
Many companies now filter ICMP traffic at their firewalls.
The WinNuke[2] refers to a remote denial-of-service attack (DoS) that affected the Microsoft Windows 95, Microsoft Windows NT and Microsoft Windows 3.1x computer operating systems. The exploit sent a string of OOB (out of band) data to the target computer on TCP port 139 (NetBIOS), causing it to lock up and display a Blue Screen of Death. This did not damage or change the data on the computer's hard disk, but any unsaved data would be lost.
Many companies now filter ICMP traffic at their firewalls.
The WinNuke[2] refers to a remote denial-of-service attack (DoS) that affected the Microsoft Windows 95, Microsoft Windows NT and Microsoft Windows 3.1x computer operating systems. The exploit sent a string of OOB (out of band) data to the target computer on TCP port 139 (NetBIOS), causing it to lock up and display a Blue Screen of Death. This did not damage or change the data on the computer's hard disk, but any unsaved data would be lost.
[1]Denial-of-service:An attempt by attackers to prevent legitimate users of a service from using that service by flooding a network, or by disrupting connections or services.
[2]Winnuke: A program that exploits the Windows TCP/IP stack causing Windows machines running an older version of the TCP/IP protocol stack to either crash or lock up.
