| Lesson 7 | Common firewall designs |
| Objective | Assess common firewall designs. |
Common Firewall Designs
Most firewall systems today are combinations of
- Packet filter: A type of firewall devices that process network traffic on a packet-by-packet basis. Packet filter devices allow or block packets, and are typically implemented through standard routers.
- Circuit-level gateway: Circuit-level gateways are similar to packet filters. The main advantage of circuit-level gateways is their ability to provide network address translation.
- Application-level gateway: Application gateways function at all four layers of the TCP/IP suite. They are typically implemented through software installed on a specialized server. Application gateways are sometimes known as proxy servers.
Common Firewall Designs
Each of the four common firewall designs creates a matrix of filters and points that can process and secure information. Four firewall designs are:- The screening router
- The screened host firewall using a single-homed bastion host
- The screened host firewall using a dual-homed bastion host
- A screened subnet
Screened subnet firewall
The most secure of the four general implementations is the screened subnet firewall (demilitarized zone) shown in the MouseOver below.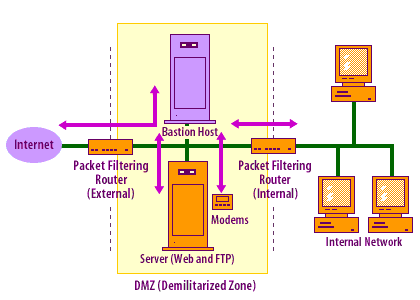
- The external packet filtering router uses standard filtering to restrict external access to the bastion host, and rejects any traffic that does not come from the bastion host. It prevents attacks such as IP spoofing and source routing.
- The bastion host constitutes a second security device that is significantly more difficult to subvert than a router.
- Incoming traffic is filtered through the external packet filtering router and then through the bastion host prior to arriving at the Web or FTP servers.
- The internal packet filtering router is also configured so that traffic flows only to or from the bastion host. It serves as a third line of defense, preventing IP spoofing and source routing. In addition, internal users cannot access the Internet without going through the bastion host.
- The internal network is effectively invisible to the Internet, because all packets going out and coming in go directly to the DMZ, not to your network.
- All publicly accessible devices, including modem pools and other resources are placed inside this zone. All packets going into and out of the internal network must pass through the DMZ. To access your network, a hacker must subvert three separate devices without being detected
Demilitarized Zone
Demilitarized zone
The screened subnet firewall uses a bastion host to support both circuit- and application-level gateways and creates a
Demilitarized zone (DMZ): Networks that are between a company's internal network and the external network. A DMZ is used as an additional buffer to further separate the public network from your internal private network.demilitarized zone (DMZ) that functions as an isolated network between the Internet and the internal network.
The use of external and internal screening routers prevents any traffic from directly traversing the sub-network, or DMZ.
