| Lesson 3 | Packet filters |
| Objective | Use packet filters as a first line of defense. |
Packet filters (First line of Defense)
A packet filter firewall is a device that inspects each packet for pre-defined content and requires extensive knowledge of TCP/IP. Engineers usually filter packets at the external router or screening router[1], which discards certain types of activity entirely. Although it does not provide error-proof protection, packet filters and/or screening routers are normally the first line of defense for a firewall strategy.
Packet filters
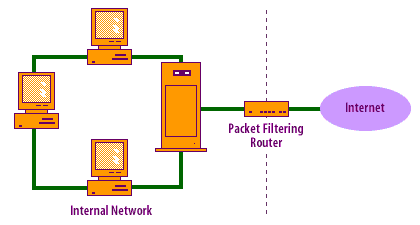
How packet filters work
Packet filters are text files composed of sequential rules that either allow or block the packet.
Packet filters are read and then acted upon on a rule-by-rule basis. Packet filters work best for restricting certain IP addresses and TCP and UDP applications from entering or leaving your network.
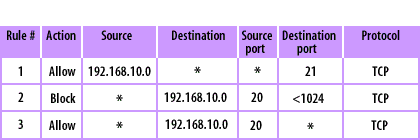
- The packet filter tells the router to filter the content of IP packets based on the source IP address, destination IP address, TCP/UDP source port, and TCP/UDP destination port fields
- In packet filtering, the rules are executed sequentially. Once a packet has failed any portion of a filter, the subsequent rules will not be read.
- The allow action routes the packet as normal if all conditions within the rule are met. The block action discards all packets if the conditions in the rule are not met. Packet filters discard any packet unless it has specifically been allowed within a rule.
- Rule 1 allows any host with the network address 192.168.10.0 to initiate a TCP session on any destination IP address on port 21.
- The second rule blocks any packet originating from any remote address with a source port of 20 and contacting a host with a network address 192.168.10.0 on any port less than 1024. If any packet meets the conditions of rule 2, it will be immediately discarded, and rule 3 will never be executed.
- The third rule allows any remote address that has a source port of 20 and is contacting any host with a network address of 192.168.10.0 on any port. Rule 3 is necessary because packet filters work by excluding all inbound and outbound traffic unless such traffic has been specifically allowed by a rule
Packet Screening
Packet filter screening
Packet filters can be used to screen entire applications or network IDs. For example, a packet filter could restrict all inbound traffic to a
specific host. This restriction would prevent a hacker from being able to contact any other host within the internal network. Screening
routers must be configured with routing tables for both the internal and the public networks. These routing tables display part of your
internal network to the outside world.
Screening router weaknesses
Packet filters take the IP addressing information at face value. If a packet passes all the rules, it will be routed to the destination. If a hacker spoofs his or her source address with a source address that is specifically allowed by a rule within the filter, the firewall will pass or route the packet.
Packet Filter Rule - Exercise
Click the Exercise button to configure a firewall using packet filter rules.Packet Filter Rule - Exercise
[1]Screening router:Examines inbound and outbound packets based upon filter rules. Screening router is another term for a packet filter.