| Lesson 2 | What is a firewall? |
| Objective | Define and describe a firewall. |
Firewalls: Protecting Your Network from Cyber Attacks
At our company, we understand the importance of network security in today's world. Cyber threats are on the rise, and protecting your network is crucial to prevent data breaches and other malicious attacks. One of the most effective ways to protect your network is through the use of firewalls.
What is a Firewall?
A firewall is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules. Firewalls act as a barrier between your network and the internet, blocking unauthorized access while allowing legitimate traffic to pass through. It is the most critical component of any security implementation and refers to the entire area between the internal network and the Internet, usually consisting of a complex series of machines and programs.
Types of Firewalls
There are several types of firewalls available, including:
- Packet-filtering Firewalls: This type of firewall filters traffic based on packet headers and specific rules.
- Stateful Firewalls: These firewalls can analyze the context of each packet and make decisions based on the state of the network connection.
- Next-Generation Firewalls: These firewalls combine traditional packet filtering with additional security features, such as intrusion prevention and malware detection.
Why Do You Need a Firewall?
A firewall is essential for protecting your network from cyber attacks. Without a firewall, your network is vulnerable to malicious traffic, which can lead to data breaches, loss of sensitive information, and other security risks.
Benefits of Firewalls
Here are some of the benefits of using firewalls:
- Protection against cyber attacks: Firewalls provide a barrier between your network and the internet, blocking malicious traffic and preventing unauthorized access.
- Enhanced network performance: Firewalls can improve network performance by blocking unwanted traffic and reducing network congestion.
- Regulatory compliance: Many industries have specific regulatory requirements for network security, and firewalls can help you meet these requirements.
At our company, we recommend using firewalls as an essential component of your network security strategy. Firewalls can help protect your network from cyber attacks, improve network performance, and ensure compliance with regulatory requirements. When choosing a firewall, consider your specific needs and budget to select the right solution for your organization. Contact us today to learn more about our network security services and how we can help protect your organization from cyber threats.
A(Firewall)-->B(Network Security); A-->C(Cyber Attacks); A-->D(Network Performance); A-->E(Regulatory Compliance);
How does a firewall provide network security?
In computer networking, a network firewall[1] acts as
a barrier against potential malicious activity, while still allowing a "door" for people to communicate between your secured network and an open, unsecured network. Originally, a firewall consisted of a single machine or "box," now referred to as a bastion host[2], that sat between a private network and the Internet.
Firewall
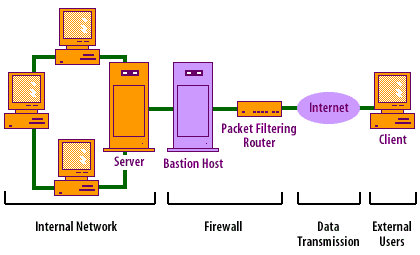
Firewall goals
The firewall should provide the following goals:
- Create Choke Point[3] used to monitor, filter, and verify all inbound and outbound traffic.
- Implement a company's security policy. For example, a security policy may state that only the Internet mail server will transmit SMTP traffic. You would enforce this policy feature directly at the firewall.
- Log Internet activity. By placing logging services at the firewalls, security administrators can monitor all access to and from the external network or Internet.
- Limit network exposure. A firewall can also enhance privacy by "hiding" your internal systems and information from the public.
Gateways
A gateway is a system that provides relay services between two devices. Gateways can range from an Internet application such as a Common Gateway Interface (CGI)[4] to a firewall gateway that processes traffic between two
hosts.
Demilitarized zones
Demilitarized zones (DMZ) are networks that are between a company's internal network and the external network.
A DMZ is used as an additional buffer to further separate the public network from your internal private network. Routers generally begin and end the DMZ.
Describe Firewall- Exercise
Click the Exercise link below to complete a short matching exercise reviewing firewall terminology.
Describe Firewall- Exercise
Describe Firewall- Exercise
[1]Firewall: A security system designed to prevent unauthorized access to or from a private network. Firewalls can be implemented in both hardware and software, or a combination of both.
[2]Bastion host: Strongly secured devices that have a direct network connection to a public network such as the Internet. It can operate as any of the three types of firewalls.
[3]Choke point: An intersection between a company's private and a public network used to monitor, filter, and verify all inbound and outbound traffic.
[4]
(CGI)Common Gateway Interface: A protocol that allows a Web server to pass control to a software application, based on a user request.
It also allows that program to receive and organize that information, then return it to the user in a consistent format. A CGI script resides on a Web server, enabling the CGI process.
