Hackers, Sniffers, and Snort
Snort's open source (NIDS) network-based intrusion detection system has the ability to perform real-time traffic analysis and packet logging on Internet Protocol (IP) networks.
Snort performs
The program can also be used to detect probes or attacks, including, but not limited to,
Snort can be configured in three main modes:
In sniffer mode, the program will read network packets and display them on the console. In packet logger mode, the program will log packets to the disk. In intrusion detection mode, the program will monitor network traffic and analyze it against a rule set defined by the user. The program will then perform a specific action based on the type of intrusion that has been identified.
- protocol analysis,
- content searching and
- matching.
The program can also be used to detect probes or attacks, including, but not limited to,
- operating system fingerprinting attempts,
- buffer overflows,
- server message block probes, and
- stealth port scans.
Snort can be configured in three main modes:
- sniffer,
- packet logger, and
- network intrusion detection.
In sniffer mode, the program will read network packets and display them on the console. In packet logger mode, the program will log packets to the disk. In intrusion detection mode, the program will monitor network traffic and analyze it against a rule set defined by the user. The program will then perform a specific action based on the type of intrusion that has been identified.
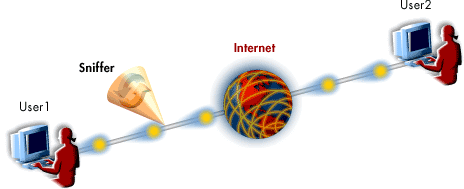
- User 1 uses sniffer to eavesdrop on User 2
- User 1 has connected to the internet using telnet, an insecure remote service
- User 1 communicates with User 2
- Sniffer is copying everything sent between User 1 and User 2