| Lesson 6 | Logfiles |
| Objective | Use logfiles for accounting and auditing. |
Use logfiles for Accounting and Auditing
Logfiles may be generated either by the default Linux installation or by installing utilities to create additional logging. These logfiles assist process accounting by retaining details that can aid in troubleshooting and detecting attacks. Normally, you can find these files in the
The default Red Hat installation provides mechanisms for gathering information on network connections. Two network logs are automatically created, one for tracking FTP connections,
Logfiles are also automatically created to keep track of what users are doing. The file
The logfiles that keep track of process executions are not created automatically for you, and must be configured into your system. Once installed and enabled, the file
var/log directory, broken up into groups relating to networks, users, and processes.
The default Red Hat installation provides mechanisms for gathering information on network connections. Two network logs are automatically created, one for tracking FTP connections,
/var/log/xferlog, and the other listing all failed remote connection attempts, /var/log/secure.
Both these files can be viewed using the less or head command, which will show you the latest additions. Logfiles are also automatically created to keep track of what users are doing. The file
/var/run/utmp provides a listing of all currently connected users, which you can view by issuing the who command. A history of all users logged in is kept in the /var/log/utmp file, and can also be viewed by issuing the who command. Viewing the files may assist you in finding people who are abusing your system. The logfiles that keep track of process executions are not created automatically for you, and must be configured into your system. Once installed and enabled, the file
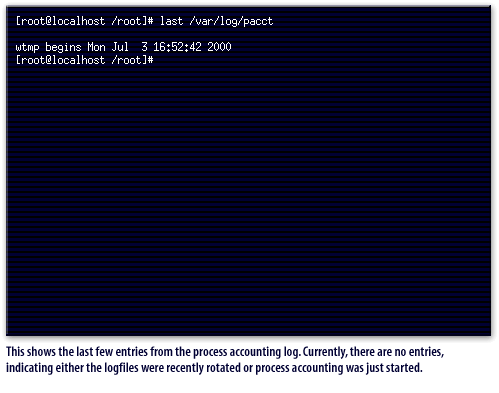
/var/log/pacct will contain the information of process execution and may be viewed by issuing the lastcomm
command. This information may be valuable in troubleshooting and security problems.
The following series of images describe what these log files look like.
Logfile Contents in Redhat Linux
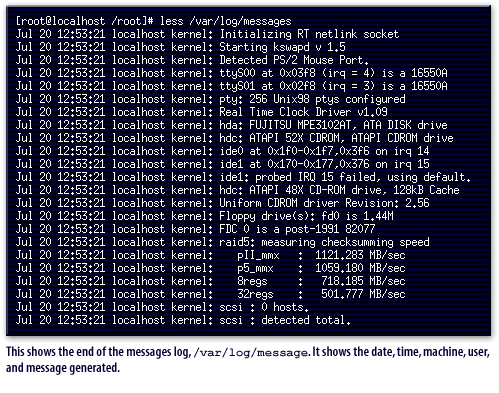
/var/log/message.
It shows the date, time, machine, user, and message generated.
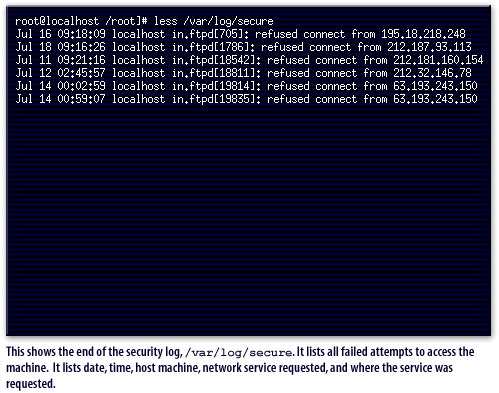
/var/log/secure. It lists all failed attempts to access the machine. It lists date, time, host machine, network service requested, and where the service was requested.
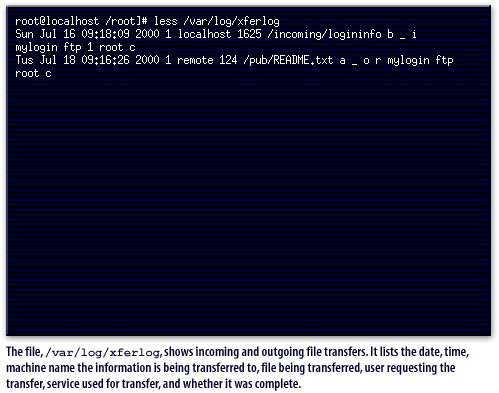
/var/log/xferlog, shows incoming and outgoing file transfers. It lists the date, time, machine name the information is being transferred to, file being transferred, user requesting the transfer, service used for transfer, and whether it was complete.
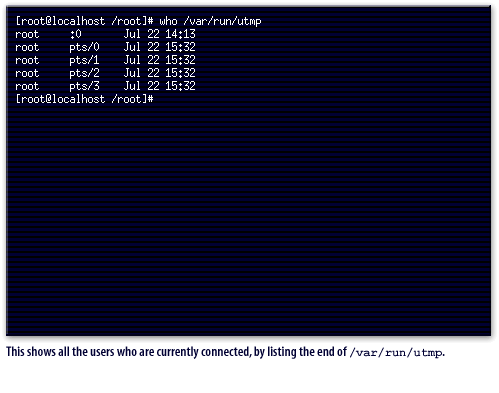
/var/run/utmp.
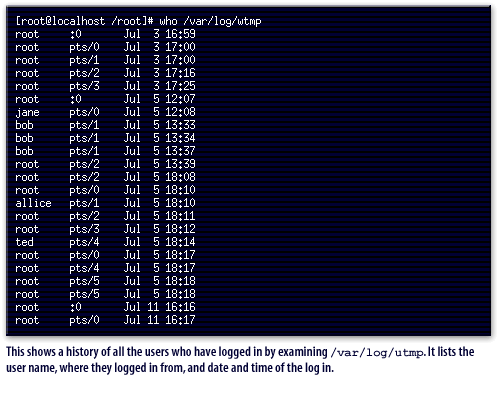
/var/log/utmp.
It lists the user name, where they logged in from, and date and time of the log in.
End of the messages log in RedHat Linux
Before moving on to the next lesson, click the link below to learn more about logfiles.
View Log Files Command
View Log Files Command
The next lesson concludes this module.
