| Lesson 6 | Application layer |
| Objective | Identify application layer and its weaknesses |
Network Application Layer
The Application Layer, the highest layer in the TCP/IP protocol suite, provides the interface for users and applications to access network services. It includes various protocols that applications use to exchange data, and it's where users directly interact with software applications. This layer essentially provides process-to-process communication over an IP network and uses protocols like HTTP, FTP, SMTP, DNS, and others.
Despite its importance, the Application Layer has several potential weaknesses:
Despite its importance, the Application Layer has several potential weaknesses:
- Application Vulnerabilities: This layer is highly susceptible to various forms of application-level attacks due to vulnerabilities within the application software itself. This includes SQL injection, Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), and others. These attacks exploit coding errors and software vulnerabilities to gain unauthorized access, steal sensitive data, or disrupt service.
- Sensitive Data Exposure: When data is transmitted in plaintext over the network, it becomes vulnerable to interception and misuse. In the absence of proper encryption measures, sensitive information (such as usernames, passwords, and credit card numbers) can be intercepted and stolen.
- Phishing and Social Engineering Attacks: These attacks manipulate users into providing sensitive information, often by masquerading as a trusted entity. Such attacks rely on human error rather than software vulnerabilities and are thus difficult to prevent entirely.
- Malware Infections: The Application Layer can be exploited to deliver malware, including viruses, worms, ransomware, and spyware. Once a device is infected, it can be used to compromise data, degrade performance, or launch additional attacks.
- Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks: These attacks overload systems, often by flooding them with excessive network traffic, rendering them unavailable to users. While DoS attacks can occur at multiple layers, many specifically target Application Layer protocols (e.g., an HTTP flood attack).
- Unprotected APIs: Applications often use APIs to communicate with each other, but these can be weak points if not properly secured. Attackers can exploit these to gain unauthorized access or to manipulate the application's functionality.
The application layer is the most difficult to secure.
Together, the TCP and UDP ports allow more than 130,000 possible applications to be used over the TCP/IP suite. Protecting a network on a per-application basis is difficult; a better approach is to allow only particular applications to communicate through the network.
Together, the TCP and UDP ports allow more than 130,000 possible applications to be used over the TCP/IP suite. Protecting a network on a per-application basis is difficult; a better approach is to allow only particular applications to communicate through the network.
TCP/IP application layer
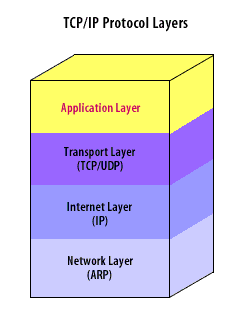
- Application Layer
- (TCP/UDP) Transport Layer
- (IP) Internet Layer
- (ARP) Network Layer
Client Applications
Hosts use a client-side application to initiate communication with other hosts. When a client establishes a TCP session with a server, it will use Ephemeral port numbers are normally between 1025 and 5000. The client will address all its TCP traffic to TCP port 80 of the Web server, the port for HTTP.
The Web server will address all its traffic to the ephemeral port of the client.
The Web server will address all its traffic to the ephemeral port of the client.
Services or daemons
The server side of a TCP/IP application is similar to the client side, except that the server application is always running.
When the host is first started, all the server applications that are configured to automatically start will begin listening for any requests addressed to their specific TCP or UDP port numbers.
For example, a user must load his or her Internet mail application to receive and send email. However, the mail server itself must always be running to allow the client to access the email application. Microsoft Windows NT calls its server applications services and UNIX calls them daemons[1].
For example, a user must load his or her Internet mail application to receive and send email. However, the mail server itself must always be running to allow the client to access the email application. Microsoft Windows NT calls its server applications services and UNIX calls them daemons[1].
Server applications
Server applications are often the target of hacker attacks. As new ones are released or current ones are modified, hackers will try to exploit weaknesses in the application. To best protect your servers from attack, know exactly which server applications are running so that you can monitor and filter inbound traffic.
A common hacker technique is to load an illicit server application on a host. The server application is designed to defeat the security structure of the host and/or network. Many tools, particularly application layer tools, are available to defeat illicit servers and services. Security at the application layer is implemented through application-level gateways known as proxy servers and will be discussed a later module.
A common hacker technique is to load an illicit server application on a host. The server application is designed to defeat the security structure of the host and/or network. Many tools, particularly application layer tools, are available to defeat illicit servers and services. Security at the application layer is implemented through application-level gateways known as proxy servers and will be discussed a later module.
[1]Daemon:A process that performs a specified operation at a predefined time or in response to certain events. Daemon is a UNIX term. In other operating systems such as Windows, daemons are referred to as services.