| Lesson 5 | Application-level gateway proxy servers |
| Objective | Describe and configure application-level gateway proxy servers. |
Application-level Gateway Proxy Servers
Application gateways monitor packets at the application level, analyzing
data as an entire message instead of individual packets. Using rules or filters, the proxy server can determine if the message contains good or
malicious data.
The technology has progressed since the dawn of the Internet. You can buy fine devices, and you can build them using free
software. When you pay for a firewall, you may get more sophisticated interfaces or more advanced application-level filtering. You may also get customer support, which is not available for the roll-your-own varieties of firewalls
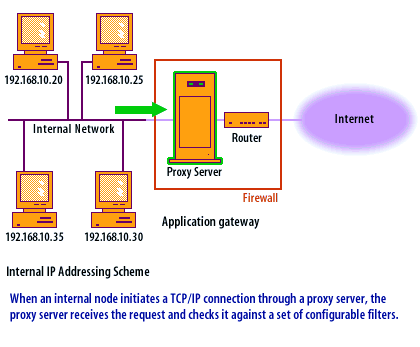
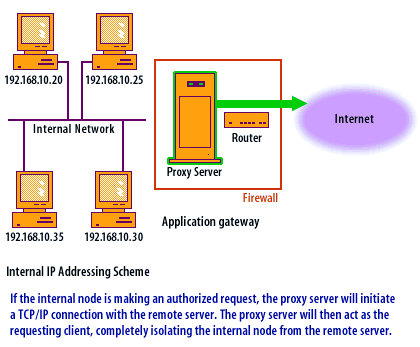
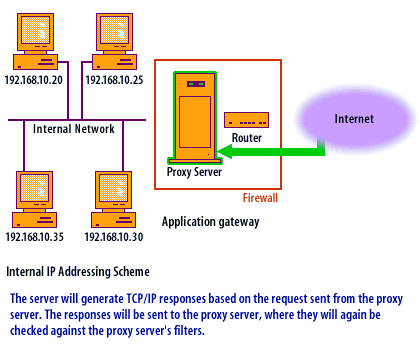
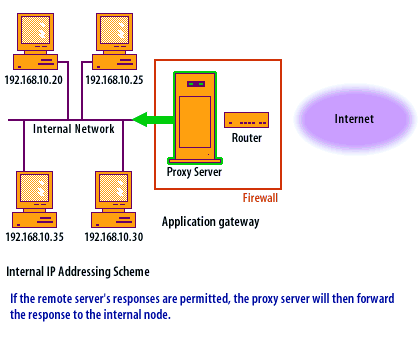
Transport Layer Protocols
When using an application-level gateway, certain transport layer protocols work better than others. Since TCP[1] is a connection-based protocol, it can easily be used through a proxy server. The proxy server applies the filters to the TCP session only when the session is initialized. During the life of the TCP session, the proxy server does not analyze the TCP header portion of the packet. UDP[2] is connectionless and each UDP packet is treated as an individual message. The proxy server analyzes each packet and applies it to the filters separately, slowing the proxy process. ICMP[3] is nearly impossible to proxy, so programs that rely primarily on ICMP messages typically do not work through an application-level gateway.
Advantages of Application-Level Gateway
Advantages of an application-level gateway are that the proxy server:
- Provides network address translation (NAT)[4]
- Features robust logging and alarming features
- Analyzes nearly every portion of a TCP/IP session
- Allows access restriction to an entire domain
- Provides Reverse proxy service: A company's registered Web or email server located outside a network's firewall system is used to prevent public users from contacting the Web server directly. When public users access the reverse proxy Web server, it contacts the Web server that resides behind the firewall. reverse proxy services
- Scans Simple Mail Transfer Protocol (SMTP): The Internet standard protocol to transfer electronic mail messages from one computer to another. It specifies how two mail systems interact, as well as the format of control messages they exchange to transfer mail.
- Monitors specific HTTP[5] and NNTP[6] traffic for restricted content
Disadvantages of Application-level Gateways
As a Network Security Administrator, it is crucial to understand the limitations and challenges associated with the deployment and management of application-level gateways (ALGs), also known as application layer gateways or proxy-based firewalls. These gateways offer high levels of security by inspecting and filtering traffic at the application layer of the OSI model, but they come with certain disadvantages:
In light of these disadvantages, it is imperative for network security administrators to carefully assess the suitability of application-level gateways in their specific network environments. Alternatives or complementary solutions, such as next-generation firewalls (NGFWs) or intrusion prevention systems (IPS), should be considered to balance security requirements with performance, scalability, and manageability.
One disadvantage of application-level gateways is that the filters for the TCP/IP applications must be configured individually. To create secure filters, firewall administrators will require extensive knowledge of all the applications and the unique settings for each. In some cases, specific proxy servers will need to be created to proxy a single application.
- Performance Impact:
- Application-level gateways can introduce significant latency and reduce network performance due to the deep packet inspection and processing required for each packet. This thorough examination of traffic can lead to bottlenecks, especially in high-throughput environments.
- Complexity in Configuration and Management:
- ALGs require detailed configuration to effectively manage and filter application-specific protocols. This granularity can lead to complex setups and necessitates a high level of expertise for proper management, making it challenging to maintain, especially in large or dynamic environments.
- Limited Protocol Support:
- These gateways are designed to understand and filter specific application protocols. If an application uses proprietary or non-standard protoc.
- Resource Intensive:
- Due to the extensive processing required for inspecting application-level content, ALGs can be resource-intensive, requiring substantial memory and CPU resources. This can necessitate more powerful hardware compared to other firewall types, increasing the cost of deployment and maintenance.
- Potential for Single Point of Failure:
- Introducing an application-level gateway into a network architecture can create a single point of failure. If the ALG experiences a failure or becomes overwhelmed by traffic, it can disrupt the entire network's connectivity, impacting business operations.
- Scalability Concerns:
- Scaling an ALG setup to accommodate growing traffic volumes can be challenging. The need for detailed inspection of application traffic means that simply adding more hardware may not linearly increase performance, often requiring a redesign or significant reconfiguration of the gateway setup.
- Encryption Challenges:
- With the increasing use of end-to-end encryption, ALGs face difficulties in inspecting encrypted payloads without implementing decryption mechanisms like SSL/TLS interception, which introduces privacy concerns and additional complexity.
- Vendor Dependence:
- Organizations may become reliant on specific vendors for their ALG solutions, leading to potential issues with vendor lock-in. This reliance can limit flexibility and choice, especially if the vendor's development path does not align with the organization's evolving security needs.
In light of these disadvantages, it is imperative for network security administrators to carefully assess the suitability of application-level gateways in their specific network environments. Alternatives or complementary solutions, such as next-generation firewalls (NGFWs) or intrusion prevention systems (IPS), should be considered to balance security requirements with performance, scalability, and manageability.
One disadvantage of application-level gateways is that the filters for the TCP/IP applications must be configured individually. To create secure filters, firewall administrators will require extensive knowledge of all the applications and the unique settings for each. In some cases, specific proxy servers will need to be created to proxy a single application.
Proxy Arrays
A proxy array is several proxy servers configured as one. Proxy arrays are also known as proxy clusters and are provided for load balancing. When several reverse proxy servers are used together, the total amount that the servers can cache is increased. The group also provides fault tolerance in case one of the proxies fails. Certain proxy arrays can also act as a single unit. For example, depending on how the proxy servers in the array are configured, changing a setting of one will change the settings on all. Proxy arrays are often used in a reverse proxy environment as well. When proxy arrays are used with a reverse proxy solution, public users can access several Web servers simultaneously.
Commercial proxy servers will normally be compatible with all current Internet applications. However, when new applications are developed, you may need to contact the vendor for an update to the proxy server to make it compatible with the new application. Always make sure that, if your proxy servers are scanning for viruses, they use the most recent virus definition file.
Commercial proxy servers will normally be compatible with all current Internet applications. However, when new applications are developed, you may need to contact the vendor for an update to the proxy server to make it compatible with the new application. Always make sure that, if your proxy servers are scanning for viruses, they use the most recent virus definition file.
[1](TCP/IP)Transmission Control Protocol/Internet Protocol: A suite of protocols that turns information into blocks of information called packets. These are then sent across networks such as the Internet.
[2](UDP) User Datagram Protocol: A connectionless protocol at the transport layer of the TCP/IP protocol stack, often used for broadcast-type protocols such as audio or video traffic.
[3](ICMP)Internet Control Message Protocol: A protocol used to communicate errors or other conditions at the IP layer
[4](NAT) Network address translation: Network Address Translation (NAT) hides internal IP addresses from the external network.
When a firewall is configured to provide NAT, all internal addresses are translated to public IP addresses when connecting to an external source.
[5](HTTP)Hypertext Transfer Protocol: A TCP/IP application that uses a browser to access and retrieve Web pages from the server.
[6](NNTP) Network News Transfer Protocol: A TCP/IP application that is one-to-many communication: a message is posted to a single location, and any number of users can contact the NNTP server to retrieve it.