| Lesson 4 | IPSec protection levels |
| Objective | Define the data protection levels provided by IPSec. |
IPSec Protection Levels
If there is a risk of unauthorized interception, you must use 1) authentication and 2) data encryption to protect the data that is sent between peers.
The options available for IPSec allow definition of the authentication and encryption protocols that are used to provide data protection.
IPSec Protection Levels Explained
IPSec (Internet Protocol Security) is a protocol suite used to secure IP communications by providing confidentiality, integrity, and authentication at the IP layer. IPSec offers several protection levels that can be used to secure network traffic:
In addition to the protection levels, IPSec also offers several encryption algorithms and key exchange protocols that can be used to further customize the security of IPSec communications. The choice of protection level, encryption algorithm, and key exchange protocol depends on the specific security requirements of the network and the available resources.
- Authentication Header (AH): AH provides authentication and integrity protection for IP packets, but does not provide confidentiality. AH can be used in scenarios where the main concern is protecting against data tampering or forgery.
- Encapsulating Security Payload (ESP): ESP provides authentication, integrity protection, and confidentiality for IP packets. ESP encrypts the payload of IP packets, but not the header information.
- Both AH and ESP: AH and ESP can be used together to provide both authentication, integrity protection, and confidentiality for IP packets. This protection level is the most secure, but also the most resource-intensive.
In addition to the protection levels, IPSec also offers several encryption algorithms and key exchange protocols that can be used to further customize the security of IPSec communications. The choice of protection level, encryption algorithm, and key exchange protocol depends on the specific security requirements of the network and the available resources.
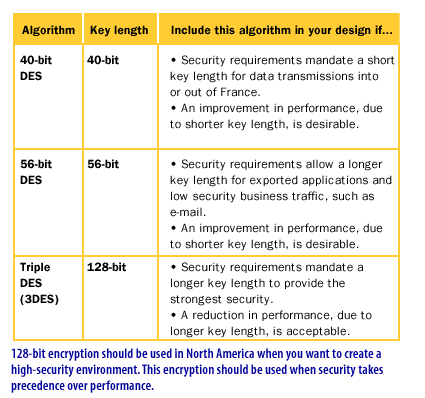
Protection levels
To reduce the CPU overhead associated with the provision of authentication and encryption, always select the lowest level of protection that meets your security requirements. The following table shows the relative protection for the supported authentication and encryption methods.
The table should be read by combining the authentication protocols, encryption, and Diffie-Hellman group on the same row. Therefore, if you combine SHA-1, 3DES, and 1,024-bit Diffie-Hellman, you have the highest level of protection. The drawback of higher protection is reduced performance, because the higher protection levels require more processor time.
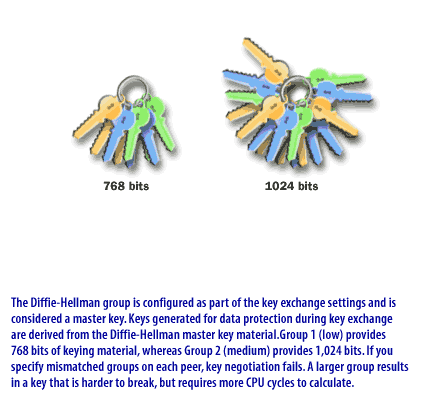
Diffie-Hellman group: Diffie-Hellman groups are used to determine the length of the base prime numbers used during the key exchange. The longer the prime number used, the more difficult it is to break the encryption code.
The table should be read by combining the authentication protocols, encryption, and Diffie-Hellman group on the same row. Therefore, if you combine SHA-1, 3DES, and 1,024-bit Diffie-Hellman, you have the highest level of protection. The drawback of higher protection is reduced performance, because the higher protection levels require more processor time.
Diffie-Hellman group: Diffie-Hellman groups are used to determine the length of the base prime numbers used during the key exchange. The longer the prime number used, the more difficult it is to break the encryption code.
| Protection | Authentication protocols | Encryption | Diffie-Hellman Group |
| **** | SHA-1 (160 bits) | 3DES (3*56 bit) | Medium (1,024 bits) |
| *** | MD5 (128 bits) | 3DES (3*56 bit) | Medium (1,024 bits) |
| ** | SHA-1 (160 bits) | DES (56 bit) | Low (768 bits) |
| * (lowest) | MD5 (128 bits) | DES (56 bit) | Low (768 bits) |
The following Slide Show elaborates on the modes of authentication and encryption.
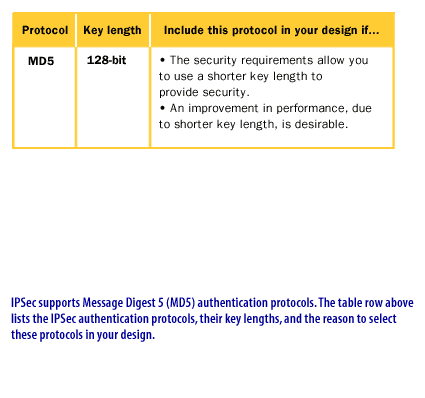
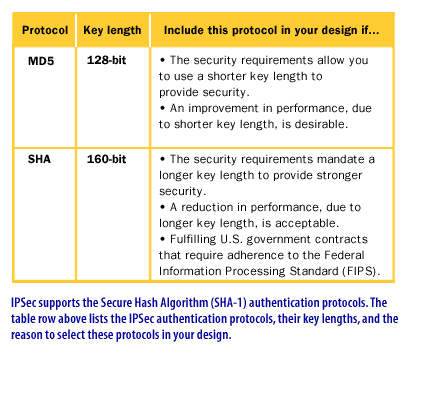
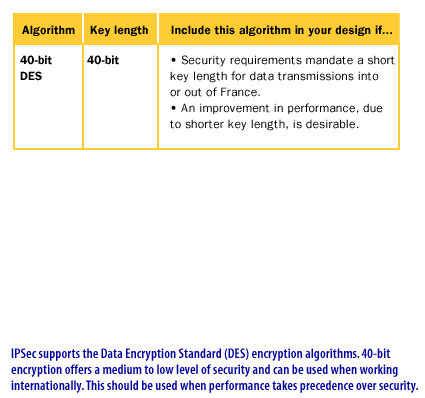
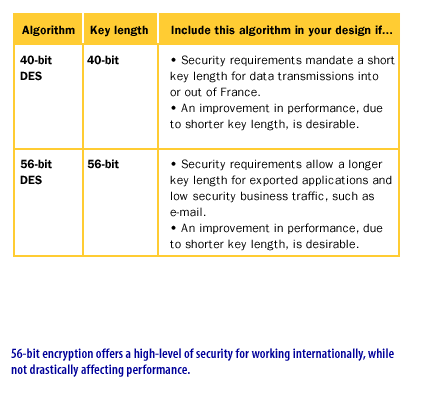
Protection Protocols
The next lesson examines IPSec Internet Key Exchange.
IPSec Protection Levels - Exercise
Click the Exercise link below to apply what you know about protecting IP traffic with filters in a Problem Solver exercise.
IPSec Protection Levels - Exercise
IPSec Protection Levels - Exercise